Why Us?
Bharat Cyber Solutions is ISO 27001 certified company.
Bharat Cyber Solutions provides a complete suite of manual and automated security testing services.
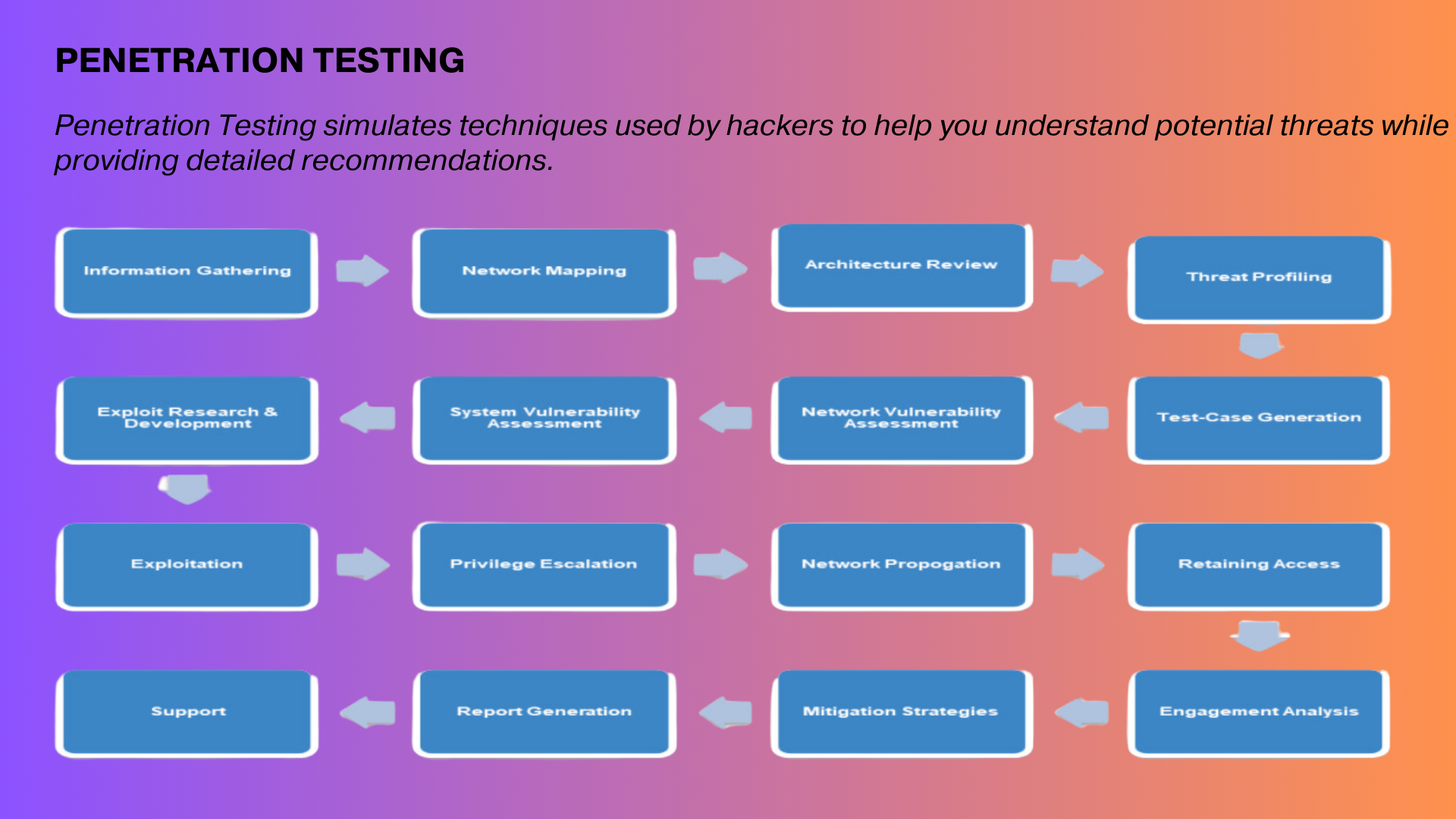
Security Testing Methodology
We perform a comprehensive five steps approach followed by complete patching(by client) and thorough re-testing in Vulnerability Assessment and Penetration Testing
What is VAPT?
VAPT stands for Vulnerability Assessment and Penetration Testing. Vulnerability Assessment examines digital assets for weaknesses and identifies security vulnerabilities. A method for identifying security holes in software or a computer network is a vulnerability assessment and penetration testing (VAPT Testing). Penetration testing exploits system flaws and alerts companies.
Why do organizations need VAPT?
Regardless of the size of the Organization, vulnerabilities exist at all levels of the IT Infrastructure (Applications, Network devices & Cloud Infrastructure). Small and medium-sized enterprises are frequently overlooked by cybercriminals is a myth as small businesses’ security is typically low, attackers gravitate towards them. In fact, 93 percent of small and medium businesses (SMEs) who have been harmed by a cyberattack say it was a serious problem. Their business will be impacted. Nearly every money and savings were reported lost. Damage was reported by 31% of people resulting in a loss of reputation clients, as well as challenges in obtaining new ones, employee retention and new business acquisition.
VAPT assists in the protection of your company by exposing security vulnerabilities in advance and providing advice on how to mitigate them. The purpose of VAPT services is to provide your company with improved security and increased financial value. For businesses aiming to comply with regulations such as the GDPR, ISO 27001, and the PCI DSS, VAPT has always been critical in providing evidence of the organization’s technology’s Security.
VAPT Certification Process
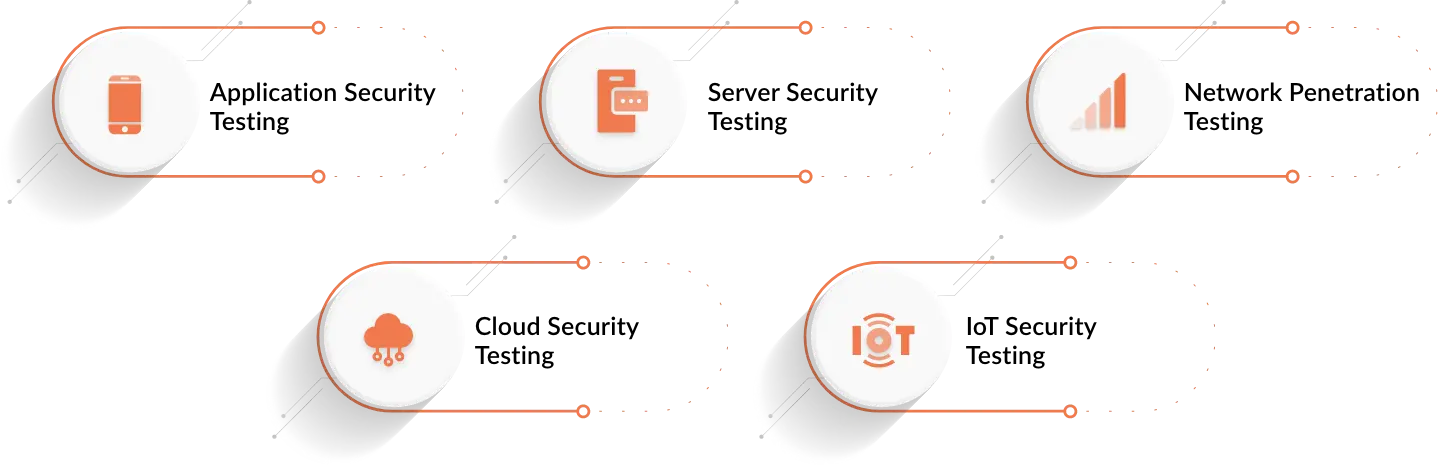
VAPT Services
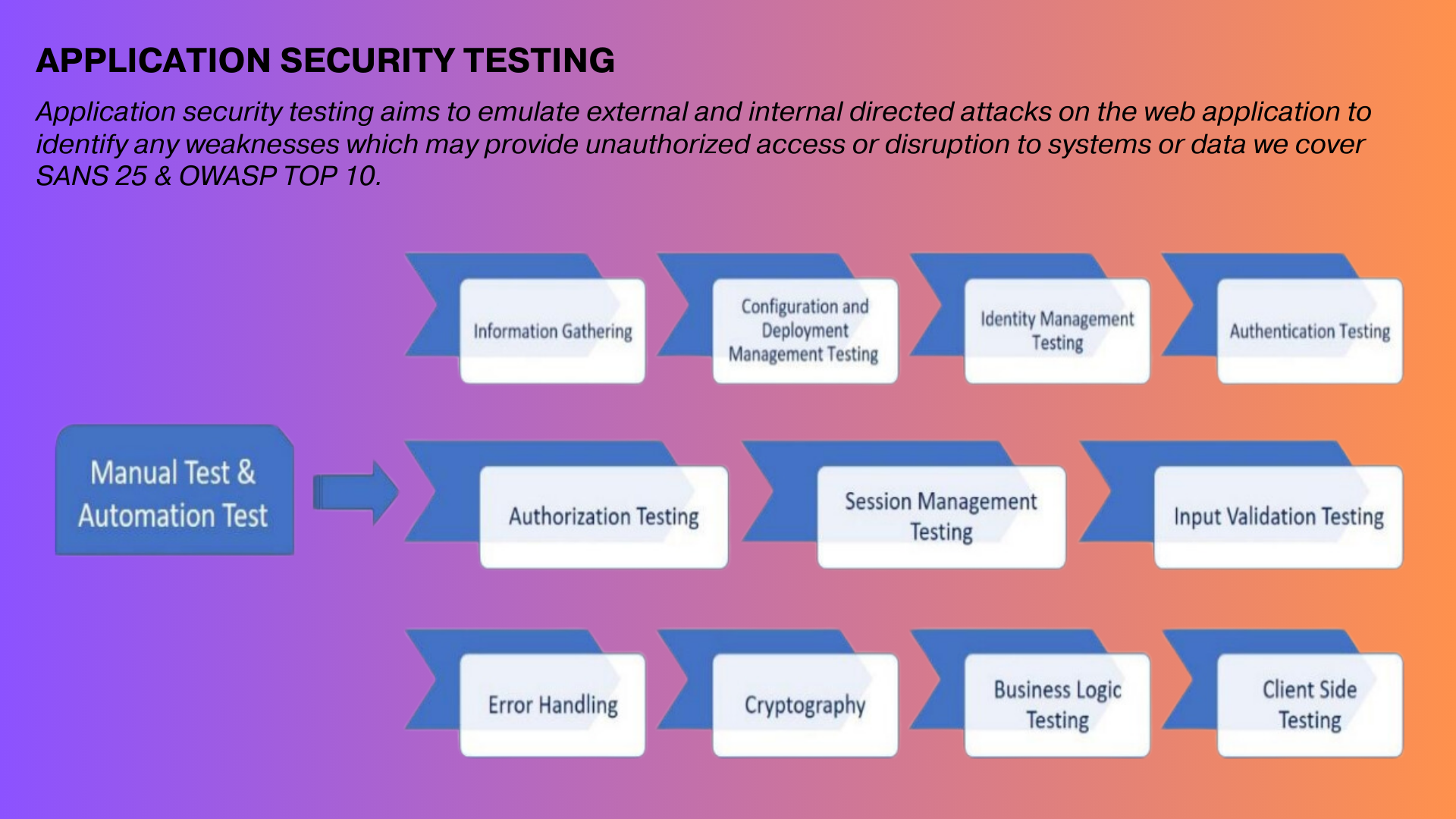
- Web Security – webapp and API : A comprehensive approach to performing penetration tests that not only finds security vulnerabilities but also business logic vulnerabilities, as well as security checklists based on industry standards such as OWASP10, SANS25, OSSTMM, and so on. Kratikal provides on-premises and off-premises application security services with the following roadmap, based on years of experience across application threat surfaces such as online, mobile, and cloud.
- Android Application Security : Ensures that your mobile applications are secure from vulnerabilities that can be exploited by attackers. This includes testing for issues like insecure data storage, unintended data leakage, weak server-side controls, and insufficient transport layer protection.
- Network Security : A network vulnerability assessment and penetration test, or network VAPT, is a technical security assessment that goes beyond the usual port scanning and vulnerability enumeration to pinpoint security risks and their business ramifications on your network, whether it be wireless, internal, or external Network Security testing is a crucial procedure that helps identify security flaws, network weaknesses, and threats that could damage any organization's networks, website servers, and other applications if they are attacked by hackers. It's a crucial step in determining how secure your network is by simulating attacks to gain unauthorized access to the target network thereby assessing the current state network security.
- Forensic: the use of specialized techniques to investigate and analyze computer systems and digital devices to gather evidence for legal proceedings or internal investigations. This process helps in uncovering, preserving, and presenting digital evidence to support cases of cybercrime, data breaches, and other security incidents.
- Automated testing : Testing involves the use of software tools to execute pre-scripted tests on a software application before it is released into production. This approach helps in identifying bugs, errors, and defects without manual intervention, ensuring the software functions correctly and efficiently.
- Cyber Law : Cyber Law encompasses the legal aspects of internet usage and governs how businesses and individuals use technology and digital platforms. It covers a broad range of issues such as data protection, privacy, intellectual property rights, and cybercrimes.